So earlier this year, I wrote (and then much later published) a blog post ripping AWS Security Hub. That led to conversations with folks on that team, and I got a chance to look at Security Hub’s new Central Configuration capabilities.
In short - this is an improvement for folks who use Security Hub and the built-in Security Standards. Sadly, it doesn’t solve many of the presentation issues that conflate “Compliance” and “Security”.
Security Hub Central Configuration
So what can this do:
- Makes it easier to deploy a standard to an entire org or OU.
- Makes it easier to disable a specific control across all accounts. For example, suppose you don’t use Hardware MFA because you’re worried your cloud engineer will leave the Yubikey at Grandma’s during a pandemic lockdown. In that case, you can disable IAM.6 everywhere and stop having that critical finding messing up the metrics.
- SecurityHub now deduplicates findings from global services, so you don’t have 17 IAM findings per account.
What does it not do:
- You must still deploy the Config Recorders in all accounts and all regions. This is a major pain.
- We still don’t see cost usage from the central region in the delegated administrator account.
- I cannot manage Integrations across accounts and regions from one place. (This workaround exists)
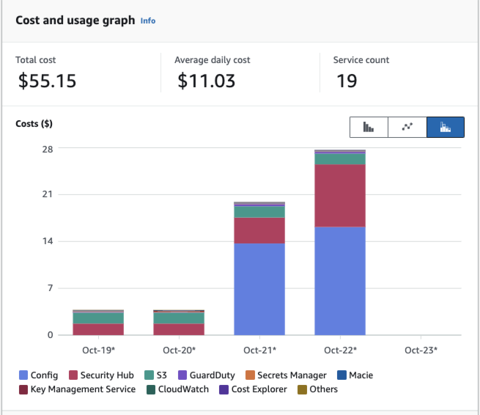
SecurityHub Standards are still expensive.
Part of the reason for that was explained as what I’d describe as a “recursion issue” with Config:
When you disable or enable a control in SecHub (regardless of whether you use Central Config to do that or the pre-existing mechanisms), it would trigger this AWS::Config::ResourceCompliance resource unless you disable it in Config. The same would happen if you were to create rules directly in Config.
That said, when you have an organization that spends only a few dollars a day, Security Hub is an expensive service, with or without Config.
AWS Config Announcements
Now, Config did make some changes that are important to note:
- You can now set some resources to periodic recording rather than on every change.
- As noted in my previous post, in June, Config got the ability to exclude resource types from recording. And it’s had the ability to explicitly define specific resource types for recording.
Unfortunately, without Delegated Admin support for Config Recorders, managing your costs with these features will be difficult at scale
Conclusions
The Security Hub team realizes the customer pain points with their dependency on AWS Config. And for a highly regulated environment, where every change must be evaluated for compliance, Security Hub is a useful tool. But as I said in my previous post, it’s best called “Compliance Hub", which is what it really measures.
My current experimentation on this topic now involves leveraging [Prowler] feeding Security Hub as an integration to see if the Insight Capability can be useful for organizations that need to contain their dumpster fire, not achieve 100% compliance.
