As has been my tradition the last few years, I prep for re:Invent by reviewing all the interesting announcements that happen in the weeks leading up to the event. This gives me a chance to keep an eye out for sessions and chalktalks related to things I care about, and a chance to corner an SA or product manager at the AWS Booth and go like this:

This year I’ll be attending AWS as a Security Hero. The good news for all 845,000 attendees is that I don’t have to wear tights. Instead I’ll be hanging out in the Heroes lounge with the other Heroes and Community Builders (hopefully sipping mimosas during the keynotes).

Since October 1st (my arbitrary start of pre:Invent season) there have been 511 announcements. Friday November 17th was the date with the largest announcement list, which goes to show AWS isn’t afraid to push to prod on Fridays (or doesn’t care about their employees weekends).
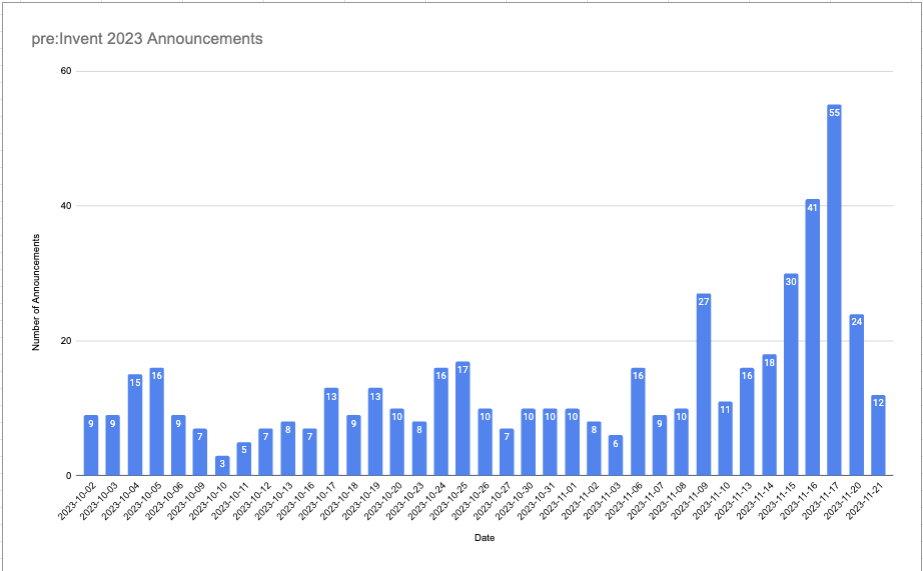
Anyway, without further ado, here are the important AWS announcements for folks who care about AWS Security & Governance.
Security Related Announcements
AWS Organizations now supports service control policies (SCPs) in AWS China Regions
Announced On: 2023-10-09
Starting today, you can use service control policies (SCPs) to set permission guardrails with the fine-grained controls used in AWS Identity and Access Management (IAM) policies in the AWS China (Beijing) Region, operated by Sinnet and the AWS China (Ningxia) Region, operated by NWCD. This feature makes it easier to meet the specific requirements of your organization’s governance rules.
Fun fact about the AWS China partition: there is no root user. Or there is no root user you have access to. With SCPs, can you now block the Chinese government from having root access to your workloads?
Amazon EC2 now supports setting AMIs to a disabled state
Announced On: 2023-10-13
Starting today, customers can disable their unused or obsolete Amazon Machine Images (AMIs; pronounced ah-mee). Disabling an AMI changes its state to disabled, makes the AMI private if it was previously shared, and prevents any new EC2 instance launches from that disabled AMI. Customers creating, managing, and consuming AMIs at-scale can now simplify and streamline their workflows with this new capability.
Someone in AWS PR just declared war with Corey Quinn with that prono. Regardless of how wrong they are, this is a useful feature to be able to sunset a-em-eyes in your environment that date back to previous presidential administrations and haven’t been supported by the vendor in years.
Announcing ability to enable AWS Systems Manager by default for all EC2 instances in an organization
Announced On: 2023-10-13
AWS customers now have the option to enable Systems Manager, and configure permissions for all EC2 instances in an organization that has been configured to use AWS Organizations, with a single action using Default Host Management Configuration (DHMC). This feature provides a method to help customers ensure core Systems Manager capabilities such as Patch Manager, Session Manager, and Inventory are available for all new and existing instances. DHMC is recommended for all EC2 customers, and offers a simple, scalable process to standardize the availability of System Manager tools.
Another reason to kill ancient AMIs is to force an upgrade to operating systems that install the SSM agent by default. I love features that allow me to manage things across multiple accounts. SSM is critical if you want to use InspectorV2.
AWS Config now supports 19 new resource types
Announced On: 2023-10-25
AWS Config now supports 19 more resource types for services, including Amazon AppStream 2.0, AWS Batch, AWS CodeBuild, Amazon CodeGuru Profiler, AWS Cloud Map, AWS Elastic Container Service (Amazon ECS), AWS Elemental MediaConnect, Amazon Inspector, AWS IoT, AWS IoT TwinMaker, AWS IoT Wireless, AWS Managed Service for Prometheus, Amazon Managed Streaming for Apache Kafka (Amazon MSK), Amazon Personalize, Amazon Route 53 Resolver, Amazon SageMaker, and AWS Transfer Family.
I recall the early days when I’d work with AWS and they’d announce pricing decreases every few quarters. Bezos’s law was nice. Now, rather than cutting prices in half every few months, all your money goes to AWS Config to run Security Hub and Control Tower.
Multi-VPC ENI Attachments
Announced On: 2023-10-26
AWS announces the general availability of multi-Virtual Private Cloud (VPC) elastic network interface (ENI) attachments for Amazon Elastic Cloud Compute (EC2) instances. With this capability, customers can now launch an instance with a primary ENI in one VPC and attach a secondary ENI from another VPC. With multi-VPC ENI attachments, customers can maintain VPC level segregation between networks, while allowing select workloads like centralized appliances and databases to communicate between them.
For security folks who may have defined a VPC as a trust boundary, this one is important to note. Your builders can now bridge VPCs together via their own EC2 machines.
AWS IAM action last accessed information for more than 60 additional services
Announced On: 2023-11-02
AWS Identity and Access Management (IAM) now provides action last accessed information for more than 60 additional services to help you refine the permissions of your IAM roles. You can use action last accessed information to identify unused permissions and refine the access of your IAM roles to only the actions they use. With this release, you can review action last accessed information for services such as AWS Auto Scaling, Amazon Redshift, and Amazon Route 53 to better adhere to the best practice of least privilege.
I’m not sure why this is exciting. Unless these API calls aren’t part of the management CloudTrail, I could have done this before.
IAM Access Analyzer policy generation now extends coverage to over 200 AWS services
Announced On: 2023-11-02
AWS Identity and Access Management (IAM) Access Analyzer policy generation has expanded support to identify actions of over 200 AWS services to help developers create fine-grained policies based on their AWS CloudTrail access activity. The new service additions include actions from services such as AWS Auto Scaling, Amazon Redshift, and Amazon Route 53. When developers initiate policy generation, IAM Access Analyzer gets to work and generates a policy by analyzing their AWS CloudTrail logs to identify actions used. For example, developers building applications might want to grant the applications permissions to access AWS resources. They can use policy generation to create a fine-grained policy and limit application role’s permissions to only those necessary. The generated policy provides developers a starting point and makes it easier for developers to grant only the required permissions to run their workloads.
One of these days I’m going to kick the tires on this capability.
AWS Config launches inventory and compliance dashboards
Announced On: 2023-11-07
AWS Config announces new inventory and compliance dashboards for AWS Config aggregators, which offer essential insights like the ‘Summary of Compliance by Resources’, ‘Top 10 accounts with noncompliant resources’, ‘Comparison of running vs. stopped EC2 instances by type’, and ‘EBS Volumes by volume type and size’.
Two trigger words in this one. Config and Compliance.
Inventory and compliance dashboards in AWS Config are now available in all supported regions at no additional cost.
When they charge an arm and a leg, not taking a few fingers isn’t exactly the best selling point.
Amazon GuardDuty introduces new machine learning capability to enhance threat detection for Amazon EKS detections
Announced On: 2023-11-09
Amazon GuardDuty has incorporated new machine learning techniques to more accurately detect anomalous activities indicative of threats to your Amazon Elastic Kubernetes Service (Amazon EKS) clusters. This new capability continuously models Kubernetes audit log events from Amazon EKS to detect highly suspicious activity such as unusual user access to Kubernetes secrets that can be used to escalate privileges, and suspicious container deployments with images not commonly used in the cluster or account. The new threat detections are available for all GuardDuty customers that have GuardDuty EKS Audit Log Monitoring enabled.
Kubernetes was the ancient Greek God of resume-padding. If you have an engineer that needs to put Kubernetes on their resume to get that FAANG job, you can enable this and find out when a ransomware group finds it public on the internet.
Amazon Elastic Block Store now supports Block Public Access for EBS Snapshots
Announced On: 2023-11-09
Amazon Elastic Block Store (EBS) now supports Block Public Access for EBS Snapshots, an account-wide security setting that allows customers to block public sharing of EBS Snapshots in an AWS Region. Customers managing EBS Snapshots at scale now have a simple and proactive way of safeguarding their data from inadvertent access by unauthorized users.
You should enable this in all your accounts. In fact, I wrote a fast-fix to do just that.
Amazon Comprehend launches new trust and safety features
Announced On: 2023-11-09
Amazon Comprehend announced new features to help organizations enhance trust and safety for text-based content. Amazon Comprehend is a natural language processing (NLP) service that provides pre-trained and custom APIs to derive insights from text. With the new Toxicity Detection and Prompt Safety Classification features, customers can now apply guardrails to moderate user and machine generated content.
I’m not clear how AWS was able to train this model after Q-Elon disabled API access to Twitter. I’m seriously wondering if I could tie this into AWS Amplify to ensure my blog posts all have a minimal level of snark and hostility to my fellow humans.
The Prompt Safety Classification features are also interesting, and I expect to see some interesting research coming out of breaking and bypassing it.
New Dashboards for edge services:
- Amazon CloudFront announces unified security dashboard
- Announcing new dashboards in AWS Web Application Firewall
AWS CloudTrail Lake announces new pricing option optimized for flexible retention
Announced On: 2023-11-15
Today, AWS CloudTrail Lake announces a one-year extendable retention pricing option that is optimized for flexible data retention needs. CloudTrail Lake is a managed data lake that lets you aggregate, immutably store, and analyze activity logs for audit, security, and operational investigations. With the one-year extendable retention pricing, the first year of retention is included with ingestion charges. You may choose to extend the retention period to a maximum of 10 years by paying extended retention charges after the first year. Compliance, audit, security, and operations teams can use the new pricing option for cost-effective retention of auditable data sources in alignment with compliance programs such as PCI-DSS, as well as for forensic and operational investigations.
This is probably the announcement that will have me revist CloudTrail Lake. Prior to this, you paid for 7 years of CloudTrail storage up front. Useful if you’re a bank with a legal requirement to do that, not useful for a meme generating company that get hacked every few months.
With this, you pay for one-year and ingestion, and you can optionally keep your events longer.
AWS CloudTrail Lake now supports CloudTrail Insights
Announced On: 2023-11-15
Today Amazon Web Services, Inc. (AWS) announces the availability of AWS CloudTrail Insights as a data source in AWS CloudTrail Lake. Until today, CloudTrail Insights were only available to customers using CloudTrail trails. Now, with CloudTrail Lake, you can analyze both your Insights events and AWS management events, helping you correlate the unusual activity with the AWS management events that could have led to it. You can also use the curated CloudTrail Lake dashboards to get an overview of anomalous behavior in your account including the type of Insights generated on your accounts or the source of these Insights.
This is the second reason to revist CloudTrail Lake.
AWS IAM Identity Center enhances the multi-factor authentication (MFA) defaults for new IAM Identity Center instances
Announced On: 2023-11-16
Starting today, all new AWS IAM Identity Center instances will have multi-factor authentication (MFA) enabled by default. Enabling MFA is a security best practice we recommend, and is one of the simplest and most effective mechanisms to help you secure your user accounts.
The best time to enable MFA was 10 years ago. The second best time is today. Glad AWS is finally moving to secure defaults.
New organization-wide IAM condition keys to restrict AWS service-to-service requests
Announced On: 2023-11-16
Today, AWS Identity and Access Management (IAM) launched two new global condition keys for IAM policies that enable you to scalably allow AWS services to access your resources only on your behalf. With this new IAM capability, you can simplify management of your resource-based policies to require that AWS services access your resources only when the request originates from your organization or organizational unit (OU) in AWS Organizations.
We got two new global condition keys aws:SourceOrgID and aws:SourceOrgPaths that can be used to ensure that AWS Services are only acting on your resources if the service is coming from your AWS Org or OU. More details at this blog post.
Amazon SQS announces support for logging data events in AWS CloudTrail
Announced On: 2023-11-16
Today, Amazon Simple Queue Service (SQS) announces support for logging data event SQS APIs using AWS CloudTrail, enabling customers to have greater visibility into SQS activity in their AWS account for best practices in security and operational troubleshooting. Amazon SQS is a fully managed message queuing service that enables you to decouple and scale microservices, distributed systems, and serverless applications.
I was shocked eariler this year to discover I didn’t have any read events for SQS - even DescribeQueues wasn’t logged. I’m glad the oldest AWS service was finally given some attention and brought up to the basic standards of 2014.
Amazon EventBridge EventBus announces support for read-only API events from CloudTrail
Announced On: 2023-11-17
Amazon EventBridge EventBus allows customers to audit and monitor the actions in their AWS environments through events that are generated by AWS CloudTrail for API calls. Previously, only mutating API calls (for example: Create, Update, or Delete) were available in EventBridge. With support for read-only API events (for example: List, Get or Describe), customers will be able to receive and process the full suite of CloudTrail events from services that are integrated with EventBridge.
Ok, this is super big. I can now get event bridge notifications when a read event occurs. This will be a boon for detection engineering teams.
AWS IAM Identity Center now provides new APIs to automate access to applications
Announced On: 2023-11-17
Today, AWS launched new IAM Identity Center APIs to manage user assignments to supported AWS and cloud applications. Together with the previously available APIs, this release allows customers to automate the management of account and application access, streamlining how customers scale with IAM Identity Center.
Till late last year Identity Center (nee SSO) didn’t even have an API for managing users in the built-in Identity Store. Now I can create that ClientVPN and federate it to Identity Center without ClickOps. Now to wait for CloudFormation Support….
Amazon S3 server access logging now supports automatic date-based partitioning
Announced On: 2023-11-21
Amazon S3 server access logging now supports automatic date-based partitioning for log delivery. Amazon S3 server access logging provides detailed records for requests made to your S3 buckets including object size, total time, turn-around time, HTTP referer, and more. Now, with date-based partitioning, Amazon S3 automatically generates either event time or delivery time prefixes when delivering access logs to your destination bucket, which allows services like Amazon Athena, Amazon EMR, and Amazon Redshift Spectrum to improve performance and reduce cost when querying logs.
If you can’t afford DataTrails, S3 server access logging is the next best thing. Now you can search specific dates rather than for all time.
Backup & Recovery
Amazon EBS announces Snapshot Lock to protect snapshots from inadvertent or malicious deletions
Announced On: 2023-11-15
Today, Amazon EBS announced the availability of Snapshot Lock, a new security feature that helps customers comply with their data retention policies and add another layer of protection against inadvertent or malicious deletions of data. Customers use EBS Snapshots to back up their EBS volumes for disaster recovery, data migration, and compliance purposes. Customers can set up multiple layers of data protection for EBS Snapshots, including copying them across multiple AWS regions and accounts, setting up IAM access policies as well as enabling Recycle Bin. With Snapshot Lock, customers can configure locks on individual snapshots so that they cannot be deleted by anyone, including the account owner, for a specified period of time. Customers have the flexibility of granting certain users access to modify snapshot lock configurations per their data governance guidelines or implementing stricter controls by ensuring that the lock configuration cannot be modified by anyone, including privileged users. Customers can also rely on this feature to store EBS Snapshots in a WORM (Write-Once-Read-Many) compliant format.
I’m not entirely sure why I’d use this over AWS Backup, but I suspect there is probably some Compliance rule that generated this feature. As for protection against a Code Spaces style attack, I’d stick with using AWS Backup.
Amazon Elastic Block Store announces default policies to backup EC2 instances and EBS volumes
Announced On: 2023-11-16
Customers can now use default policies to backup all EC2 instances and EBS volumes in their account with a single API call via Amazon Data Lifecycle Manager. Default policies work in conjunction with customers’ existing backup mechanisms to only create EBS-backed AMIs and EBS Snapshots of instances and volumes with no recent backups. This helps ensure customers have comprehensive backup protection without creating duplicate backups or increasing management overhead and cost.
This however might be a more cost-effective solution for ransomware recovery that AWS Backup. I honestly have no idea the difference between Data Lifecycle Manager and AWS Backup. Why one over the other? ChatGPT gave me the answer, but I still feel like Data Lifecycle Manager was an excuse to split a two pizza team that got one pizza too big.
AWS Backup launches new console experience with jobs dashboard
Announced On: 2023-11-16
Today, AWS Backup announces a new jobs dashboard console experience, simplifying backup health monitoring at scale with a new visual user interface and aggregated backup, copy, and restore metrics for services supported by AWS Backup.
Interesting if you use that service.
Amazon S3 now supports enabling S3 Object Lock on existing buckets
Announced On: 2023-11-20
Amazon S3 now allows you to enable S3 Object Lock for existing buckets with just a few clicks and to enable S3 Replication for buckets using S3 Object Lock. These improvements make it even easier to adopt S3 Object Lock, which protects objects from being overwritten or deleted.
Object Lock is one of those “you better get it right the first time” features that I’m always too fearful to play with. I expect to see object lock feature prominently in future ransomware attacks where the company didn’t pay the ransom, so instead they’re paying S3 charges for the next 100 years.
Governance and FinOps Related Announcements
We can start with the announcement that AWS is going to create a European Sovereign Cloud, presumably because Europe still has an anachronistic obsession with Kings and Queens. As I observed last year Sovereign Cloud is trending because the US Government was short sighted and lost the trust of west with it’s surveillance obsession.
Introducing Recover into Existing Instance for AWS Elastic Disaster Recovery
Announced On: 2023-10-16
Today, AWS Elastic Disaster Recovery (AWS DRS) announces the general availability of Recover Into Existing Instance, which allows you to recover into an original or pre-defined existing instance instead of spinning up a new Amazon EC2 instance.
AWS announces member account level credit sharing preferences
Announced On: 2023-10-19
Starting today, AWS is launching new options for credit sharing. The Billing preferences page of the Billing Console now allows you to manage credit sharing preferences for your organization at a more granular level by selecting which accounts from your organization to share your credits with and exclude others from sharing.
This is an interesting one and could be useful when applying credits in a large org.
AWS Fault Injection Simulator announces scenarios and scheduled experiments
Announced On: 2023-11-07
Today, AWS announces the general availability of scenarios and scheduled experiments for AWS Fault Injection Simulator (FIS). Scenarios define events or conditions that customers can apply to test the resilience of their applications, such as the interruption of compute resources on which the application is running. Scenarios are created and owned by AWS, and minimize undifferentiated heavy lifting by providing you with pre-defined targets and fault actions (e.g., gradually increase CPU load from 90% to 100% for Amazon EC2 instances) for possible application impairments.
No word if “engineer pushed a change to S3 in us-east-1” is one of those scenarios.
AWS Control Tower now supports tagging for controls enabled in AWS Control Tower
Announced On: 2023-11-10
AWS Control Tower customers can now configure tags for the controls that they have enabled in AWS Control Tower. Customers can add, remove, or list tags for the controls in the AWS Control Tower console or by using the tagging APIs. Tags can help you manage, identify, organize, search for, and filter resources. You can create tags to categorize resources by purpose, owner, environment, or other criteria. AWS Control Tower now supports the following tagging APIs:
- TagResource - This API call adds tags to controls enabled in AWS Control Tower.
- UntagResource - This API call removes tags from controls enabled in AWS Control Tower.
- ListTagsForResource - This API call returns tags for controls enabled in AWS Control Tower.
I’ll just leave this here for anyone who is unfortunate enough to live in a Control Tower. I may have something out soon to rescue you, Rapunzel.
Amazon Connect prompts configuration page provides CloudTrail coverage
Announced On: 2023-11-10
Amazon Connect launches a new prompts configuration UI with an enhanced user experience and AWS CloudTrail coverage. Prompts are audio files like on-hold music that can be customized and configured to play within call flows. Now when you add, update or delete a prompt from the Amazon Connect admin website, a record of that activity is available in AWS CloudTrail for visibility, reporting, and compliance. For example, you may notice a discrepancy in the IVR prompt that customers hear when they call your support line. To investigate, you can leverage AWS CloudTrail to answer questions such as, “who saved this recording?” and, “when was this prompt changed?” To learn more about the new prompts page, see the Amazon Connect Administrator Guide and the AWS CloudTrail Documentation.
I like how they buried the “We didn’t support CloudTrail till now” on a Friday night and as part of another feature announcement.
AWS Resource Explorer now supports multi-account resource search
Announced On: 2023-11-14
Today, AWS announces the general availability of multi-account search for AWS Resource Explorer. Now, you can search for and discover resources such as Amazon Elastic Compute Cloud (Amazon EC2) instances, Amazon Kinesis streams, and Amazon DynamoDB tables across regions and across accounts in your organization using AWS Organizations. Multi-account search in Resource Explorer is available at no additional charge.
Last year I reviewed this service at Steampipe, and called out that while it was nice to look across regions, lack of AWS Organization support made it mostly useless. Now that the Orgs support is available, and they have 86 new resource types, it might be useful. You can find more details on their Blog Post
AWS Resource Explorer supports 86 new resource types
Announced On: 2023-11-15
AWS Resource Explorer now supports 86 more resource types from services including AWS CloudFormation, AWS Glue, and Amazon SageMaker. With this launch, customers can now use AWS Resource Explorer to search for and discover resources for the following newly supported resource types:
AWS Trusted Advisor announces new APIs
Announced On: 2023-11-17
AWS Trusted Advisor introduces new APIs to enable you to programmatically access Trusted Advisor best practice checks, recommendations, and prioritized recommendations. Trusted Advisor continuously evaluates your AWS environment using best practice checks in the categories of cost optimization, performance, resilience, security, operational excellence, and service quotas, and recommends actions to remediate any deviations from best practices. Trusted Advisor Priority provides context driven and prioritized recommendations from your AWS account team to help you focus on the most important recommendations.
I don’t find Trusted Advisor to be remotely useful in the environments where I have Enterprise Support, and the APIs aren’t available in the smaller environments. So Trusted Advisor is pretty much useless to me. I can get the same functionality via a CSPM (even Security Hub)
Serverless and other cool stuff
AWS CodeBuild now supports AWS Lambda compute
Announced On: 2023-11-06
AWS CodeBuild customers can now use AWS Lambda to build and test their software packages. AWS CodeBuild is a fully managed continuous integration service that compiles source code, runs tests, and produces ready-to-deploy software packages.
A lot of folks in the Community Builders and Heroes community were excited about this. My reaction was:

I suppose it’s another way to cryptomine in a customer’s account.
Deploy your stack sets faster with ConcurrencyMode in AWS CloudFormation
Announced On: 2023-11-09
AWS CloudFormation StackSets announces a new capability ConcurrencyMode that provides customers a faster deployment experience while balancing deployment safety. Customers control speed and safety of their stack set deployments with concurrency and failure tolerance. Customers define these parameters along with ConcurrencyMode as a part of their StackSetOperationPreferences prior to running a stack set operation. StackSetsOperationPreferences is available with the following six APIs: create-stack-instances, delete-stack-instances, detect-stack-set-drift, import-stacks-to-stack-set, update-stack-set and update-stack-instances. With the ConcurrencyMode parameter, customers can modify existing deployment behavior of stack set operations for faster deployments that decouples concurrency from failure tolerance.
Delegated Admin StackSets are an awesome feature for security to ensure artifacts are automatically pushed to all AWS accounts. At the 100+ account scale, pushing something to all regions wasn’t scalable. I look forward to testing these new features out soon.
Customizable action buttons are now available in AWS Chatbot
Announced On: 2023-11-13
Today, AWS announces the general availability of customizable actions in the AWS Chatbot. Actions are configurable buttons displayed on the AWS service event notifications in Microsoft Teams and Slack channels. AWS customers can include actions on service event notifications to operationalize their frequently used DevOps runbook processes and incident response tasks to shorten diagnosis and resolution cycle time.
Be careful what you allow your builders to do here. Slack probably has a different security profile from your production AWS Infrastructure. Understand what impact to AWS there is when you have a threat actor in slack.
AWS Step Functions now supports restarting workflows from failure
Announced On: 2023-11-15
AWS Step Functions now allows you to easily restart workflows from their point of failure, so you can recover from failure faster, increase efficiency, and pay only for what you need. AWS Step Functions is a visual workflow service capable of orchestrating 11,000+ API actions from over 220 AWS services to automate business processes and data processing workloads.
This one is a pretty big deal for those of use who build complex workflows using Step Functions. I’ve often had to ensure that functions run idempotently to allow me to re-run the execution from scratch. I’m looking forward to leveraging this with the next app I build.
AWS Lambda introduces new controls to make it easier to search, filter, and aggregate Lambda function logs
Announced On: 2023-11-16
AWS Lambda announces advanced logging controls that enable you to natively capture logs in JSON structured format, adjust log levels, and select the Amazon CloudWatch log group for your Lambda functions.
This is a pretty major change to how Lambda has done logging since 2014. You can now write your log messages exclusively as JSON. The Lambda service now supports the concept of a logging level, so no more setting that via environment variables. Plus you can split the logging level for the logs you write from the logs Lambda writes. You can also customize the name of the CloudWatch Log Group! More details at their Blog Post I’m glad all these have native CloudFormation and SAM support.
This may have major considerations for everyone’s lambda logging collection into SIEMs
It’s also worth noting the AWS Lambda console now features a single pane view of metrics, logs, and traces
Introducing Amazon CodeWhisperer for command line (preview)
Announced On: 2023-11-20
Today, AWS announces the preview of Amazon CodeWhisperer for command line. CodeWhisperer now helps developers be more productive in the command line with contextual CLI completions and AI natural-language-to-bash translation.
Ok, not specifically serverless or serverful - this is the fig.io acquisition. It runs on your local workstation, and makes lots of API calls out to various services to help builders be more productive. Super cool stuff here, but you really want to read the T&Cs here.
Services now supporting new Security features
I don’t have much to say on any of these, but there here for completeness:
- Amazon Connect now enables scanning of attachments for malware
- AWS Elastic Load Balancing introduces IAM condition keys for encryption and access controls
- Amazon CodeCatalyst now supports single sign-on using AWS IAM Identity Center
Random Roundup of other stuff.
- AWS has a new CISO, coming from Capital One, so perhaps that explains the push to IMDSv2.
- AWS published a blog post on how GenAI and AWS services will all work together.
